Access experience pattern
Access Overview
The Access experience pattern leverages digital credentials to simplify and secure the way users access services online or in-person. By utilizing digital credentials stored in a digital wallet, users can seamlessly prove their identity or attributes without relying on traditional usernames and passwords or physical IDs. This approach enhances user convenience and strengthens security across various digital interactions.
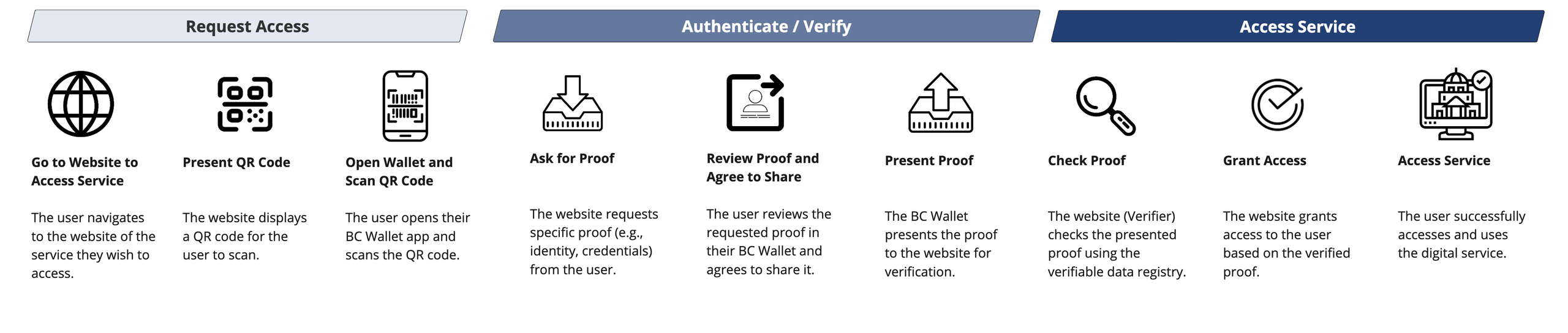
How it works Digital Trust Access enables users to securely and seamlessly access services online or in person using verifiable digital credentials. The process involves three key steps: Request, Verify, Access.
Request: The user initiates the process by navigating to the service website and scanning a QR code using their BC Wallet.
Verify: The service requests proof of identity or credentials, which the user reviews and shares through their BC Wallet.
Access: The service validates the credentials via the verifiable data registry and grants the user access to the digital service.
Technology Required:
- BC Wallet: A secure digital wallet application for storing and managing digital credentials.
- Digital credential(s): A cryptographically secure and verifiable proof of identity or attributes.
- Your digital service: The service being accessed, which relies on digital credentials for authentication.
Benefits
Problem: Traditional access methods, such as usernames and passwords, present significant security vulnerabilities and are often cumbersome for people. These methods are prone to data breaches, phishing attacks, and require extensive management for password recovery and updates.
Benefits: Digital credentials address these issues by providing a more secure and user-friendly authentication method. They offer cryptographic assurance, reducing the risk of data breaches and identity theft. Additionally, digital credentials streamline the access process, improving the overall user experience and aligning with best practices in digital identity management.
Suitable use cases
The BC Government offers a variety of solutions for accessing services online or in person, with digital trust and credentials emerging as innovative methods to enhance and complement existing systems. Digital trust solutions provide flexible and secure access, making them suitable for a range of applications.
Consider Digital Trust If:
- New or Existing Services: Digital trust is valuable for both new and existing services, providing secure access and extending into other experiences like signing, issuing, and messaging through BC Wallet app.
- Leveraging Existing Credentials: There are existing digital credentials that can be integrated into your service. If your service requires the issuance of a new credential, that is also possible (see the Issue experience pattern.)
- Team and Buy-in: Your organization has the appropriate team and buy-in to lead the adoption of digital trust, ideally agile teams with an appetite for experimentation and innovation.
For a detailed comparison of B.C.'s identity solutions, visit the Digital Trust website.
Technology stacks
There are different digital credential authentication solutions your digital service can leverage.
| VC-AuthN & Pathfinder SSO | Traction | BC Wallet Verify feature | |
|---|---|---|---|
| Description | Verifiable Credential Authentication via OpenID Connect (VC-AuthN) is ready made using a standardized system | Traction is a customizable digital wallet solution that can both issue, hold and verify digital credentials | Mobile verifier is a feature within the BC Wallet app that can authenticate people in-person |
| Devices | Used on web and mobile | Can integrate with web and mobile applications | Used on mobile only |
| Implementation requirements |
| Requires more time and resources to set up as well as ongoing maintenance |
|
| Customization | Low - Can use existing and customize proof requests | High- Can customize flows to meet your needs | Low - Can use existing and customize proof requests |
| Suitability |
| Your service needs to scale and integrate with different organizations and services |
|
| Capabilities | Can leverage existing proof requests and digital credentials | Can issue, holder, and verify digital credentials |
|
Examples
Below are examples illustrating the Access pattern through a sequence diagram and a real-world case study.
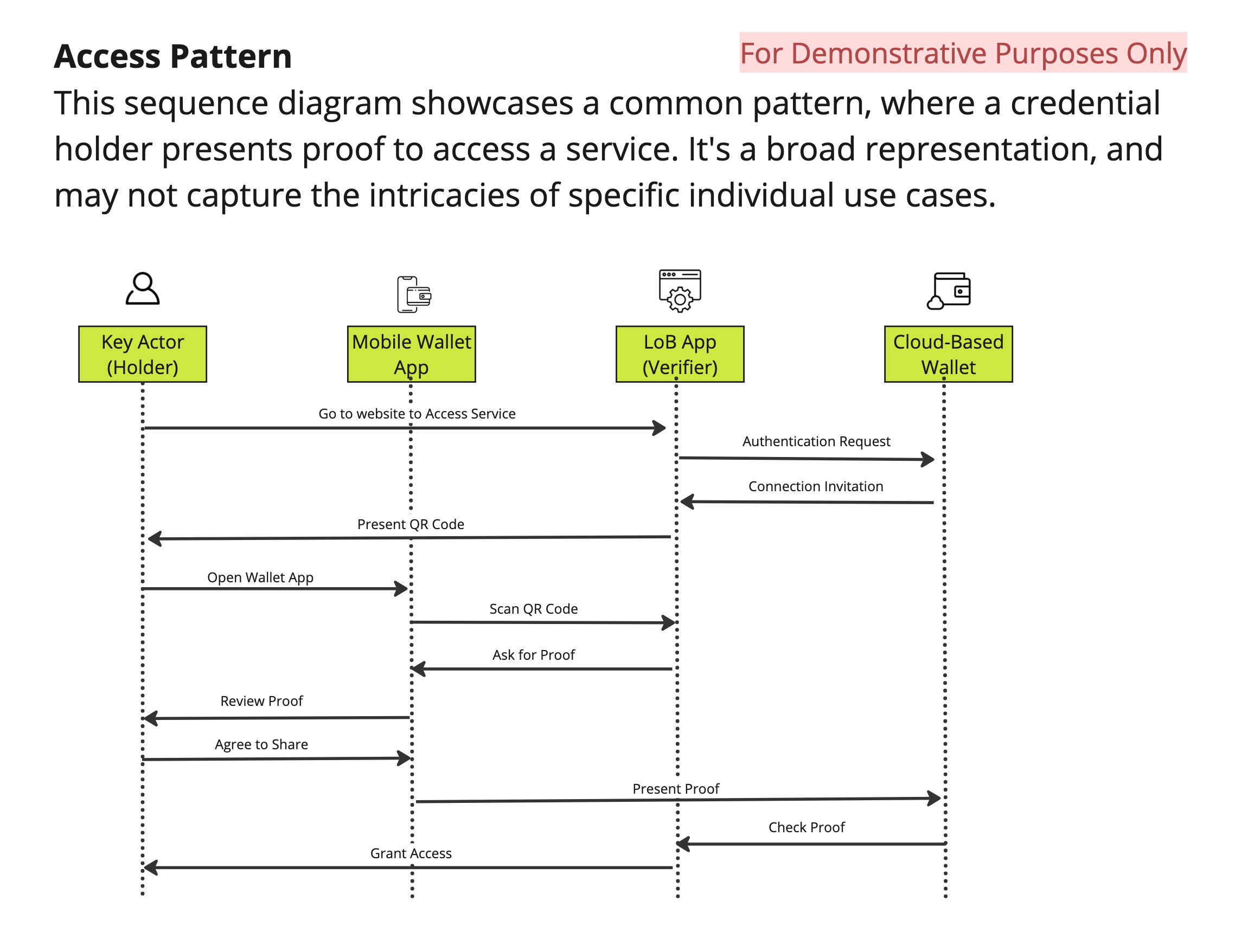
Traction Sequence Diagram Example
The following sequence diagram visualizes the Access pattern using digital credentials using Traction. It demonstrates the process of a person (Holder) accessing a service (Verifier) with a digital credential issued in their BC wallet.
VC-AuthN example - Access to Court Materials
A practical implementation of Access using VC-AuthN is showcased in the justice sector. Lawyers use a combination of digital credentials to access court materials securely, enhancing efficiency and privacy. Watch on YouTube
Get started
1. Align
Assess the suitability of digital trust for your service by considering security requirements, user needs, and the potential benefits. Assemble an agile team ready to innovate and experiment.
2. Discover
Research user needs and gather insights from stakeholders to understand how digital credentials can enhance user experience and address specific challenges.
Proof request design best practices →
3. Trial
Implement and test the digital trust solution, conducting pilot trials to validate the approach and refine the implementation based on feedback.
4. Scale
Launch the digital trust solution broadly, monitor its performance, and plan for scaling to cover additional services or a broader user base, ensuring continuous improvement.
Complete the Scale phase (TBD) →
Resources
- Play with the BC Wallet showcase to explore how digital credential verification can work Becoming a Verifier →
Contact
For further assistance contact the Digital Trust Team.